Security Advisory: Log4j v2 Vulnerability (CVE-2021-44228)
| Last Updated | 03 Jan 2022 |
|---|
Peer Software has been monitoring the news around the recently published remote code execution vulnerability that involves the Apache Log4j v2 library (CVE-2021-44228).
This vulnerability does not affect any of our products. More details can be found below.
| Product/Tool | Version(s) | Status | Description |
|---|---|---|---|
| Peer Global File Service | All | Not impacted | PeerGFS does not use Log4j v2, nor does it use Log4j's JMSAppender (noted in CVE-2021-4104) or SocketServer (noted in CVE-2019-17571). |
| PeerLink | All | Not impacted | PeerLink does not use Log4j v2, nor does it use Log4j's JMSAppender (noted in CVE-2021-4104) or SocketServer (noted in CVE-2019-17571). |
| PeerSync | All | Not impacted | PeerSync does not use Log4j. |
| PeerLock | All | Not impacted | PeerLock does not use Log4j. |
| File System Analyzer | All | Not impacted | File System Analyzer does not use Log4j. |
| File Activity Analyzer | All | Not impacted | File Activity Analyzer does not use Log4j. |
| Health Checker | All | Not impacted | Health Checker does not use Log4j. |
Some additional notes on this and related vulnerabilities:
- We have seen some scanners that label the Log4j library used in PeerGFS and PeerLink as being impacted by this vulnerability.
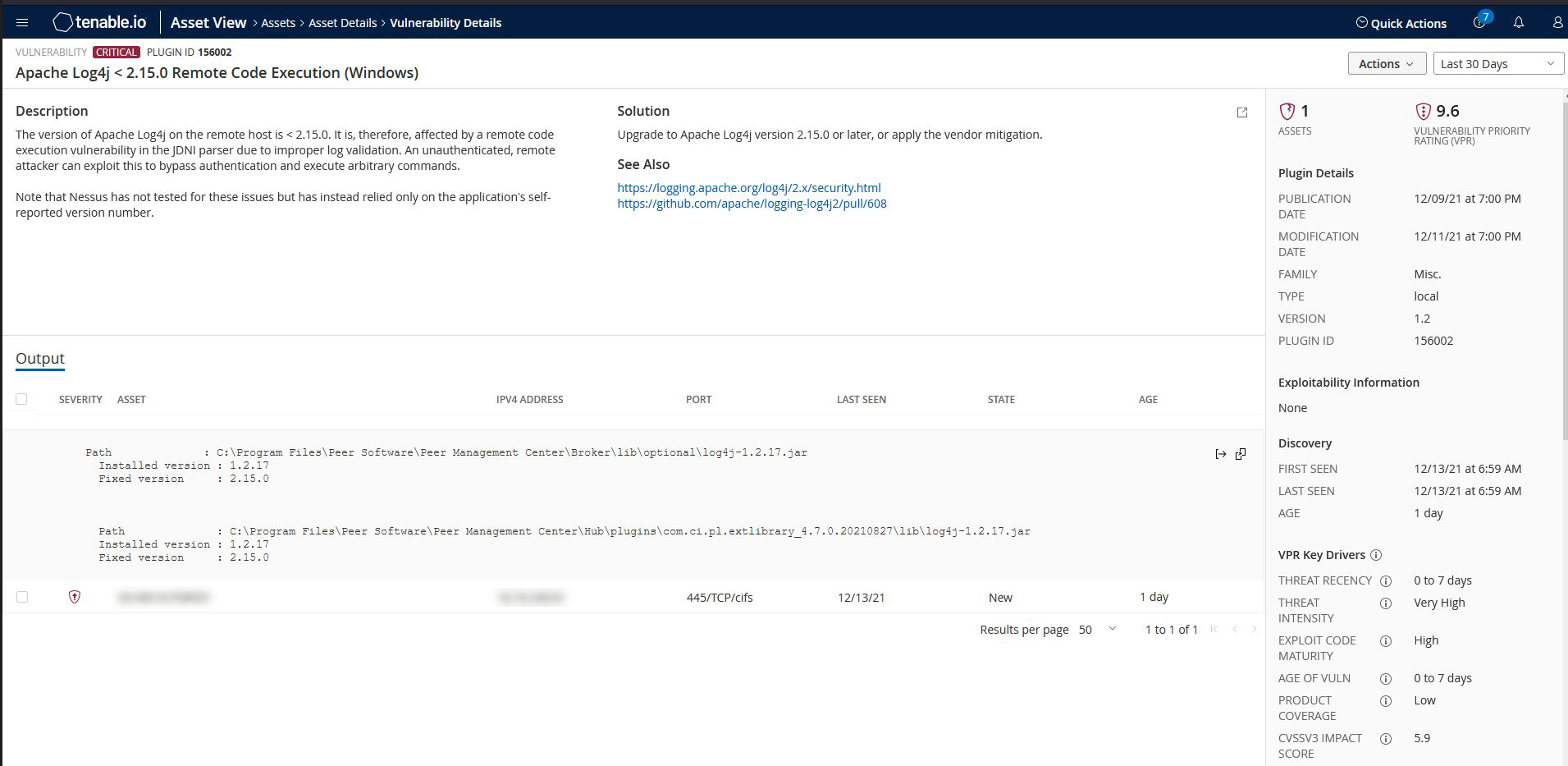
On closer investigation, it appears that some scanners are simply looking for any version of Log4j that is less than 2.15.0. Based on research and feedback from the Log4j development team, this particular vulnerability only impacts Log4j v2. It does not apply to Log4j v1 and as such, does not apply to PeerGFS and PeerLink. - Some scanners may pick up on a pair of Log4j v2 libraries that are bundled with the new Peer Management API service in PeerGFS v4.6 and above. Log4j v2 provides a logging API in addition to a core logging engine. The core logging engine library is the one impacted by this vulnerability. The libraries bundled with PeerGFS (log4j-api-2.x and log4j-to-slf4j-2.x) are tied to the Log4j v2 API only, not to the core logging engine. As such, this vulnerability does not apply to the Peer Management API service and PeerGFS.
- There is a similar CVE (CVE-2021-4104) now posted for Log4j v1's JMSAppender functionality. As shown in the table above, PeerGFS and PeerLink do not use this JMSAppender functionality and as such, this related vulnerability does not apply.
- Log4j v1 does have a critical vulnerability in it (CVE-2019-17571). However, as shown in the table above, PeerGFS and PeerLink do not use this SocketServer functionality and as such, this vulnerability does not apply.
- A related vulnerability has been reported for Log4j v2.15.0 (CVE-2021-45046). As shown in the table above, PeerGFS and PeerLink do not use Log4j v2 and as such, this related vulnerability does not apply.
- A related vulnerability has been reported for Log4j v2.16.0 (CVE-2021-45105). As shown in the table above, PeerGFS and PeerLink do not use Log4j v2 and as such, this related vulnerability does not apply.
- A related vulnerability has been reported for Log4j v2.17.0 (CVE-2021-44832). As shown in the table above, PeerGFS and PeerLink do not use Log4j v2 and as such, this related vulnerability does not apply.
If you have additional questions, please contact our support team via Peer Service Desk.
