Problem replicating NTFS permissions
Problem
PeerSync is having problems trying to replicate NTFS permissions.
Solution
Follow these troubleshooting steps:
- PeerSync should have the admin backup option enabled (Advanced Options page > check Admin Backup). This is the standard method for PeerSync to replicate files and folders when its service account does not have explicit permissions to these files and folders.
By default, if the PeerSync service account is a member of the local group “Administrators”, it should have the necessary privileges to allow the Admin Backup to work. If the service account is NOT a member of the local “Administrators” group on both the source Windows 2003 Server and the target 7-Mode filer/vfiler, add it to both.
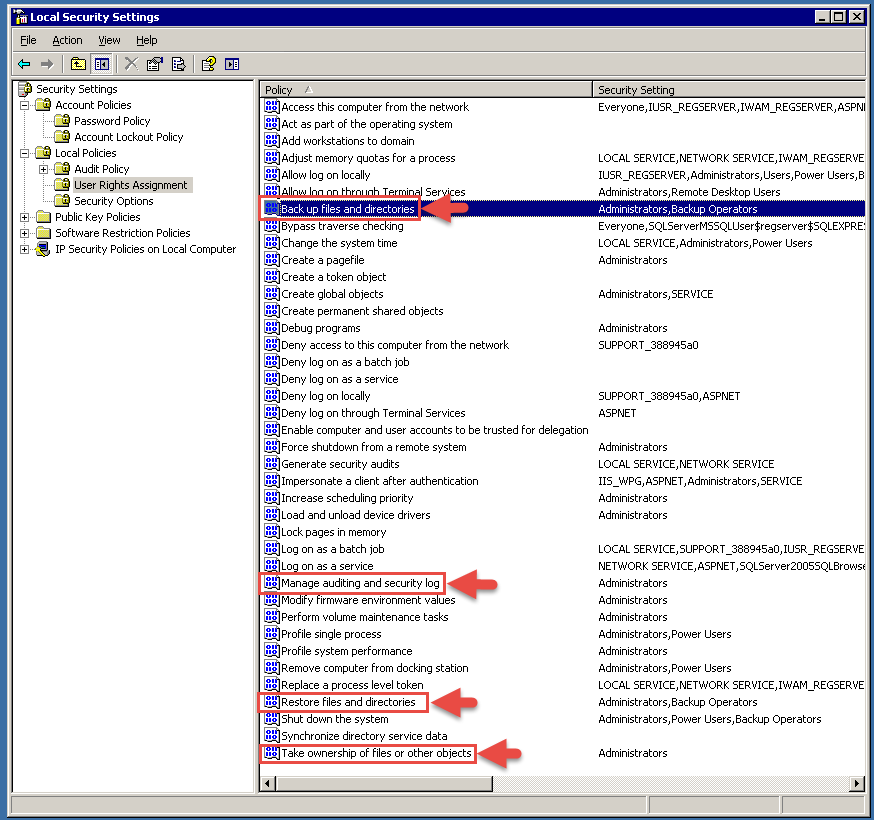
If steps 1 and 2 are complete but PeerSync is still unable to replicate permissions, it’s possible that the local “Administrators” group is locked down and does not have the appropriate privileges. These are required:
Back up files and folders – “SeBackupPrivilege” – allows PeerSync to read from the source even when its service account does not have explicit permissions
Restore files and directories – “SeRestorePrivilege” – allows PeerSync to write to the target even when its service account does not have explicit permissions
Manage auditing and security log – “SeSecurityPrivilege” – allows PeerSync to read and write permissions on files and folders even when its service account does not have explicit permissions to do so
Take ownership of files or other objects – “SeTakeOwnershipPrivilege” – allows PeerSync to set ownership on files and folders even when its service account does not have explicit permissions to do so
- For Windows, this Local Security Policy screenshot shows where these settings can be configured. These can also be set via Group Policy.
- For NetApp 7-Mode, we haven’t found any explicit commands to add these privileges to either the local “Administrators” group or to set them for individual users. Group Policy will likely be the only way to set these privileges.
- For NetApp cDOT, to grant these privileges to the account DOMAIN_USER_NAME (in the format “DOMAIN\USERNAME”) on SVM SVM_NAME, use the following ONTAP command from the cluster context:
- For Windows, this Local Security Policy screenshot shows where these settings can be configured. These can also be set via Group Policy.
vserver cifs users-and-groups privilege add-privilege –vserver SVM_NAME –user-or-group- name DOMAIN_USER_NAME –privileges SeBackupPrivilege, SeRestorePrivilege, SeSecurityPrivilege, SeTakeOwnershipPrivilege
